How to prevent hackers from hacking your facebook account - A most read for facebook users
A lot of people fall victims of facebook account hack. I am writing this post just to educate people on how to secure their facebook account from being hacked. Many facebook users fall victims of such hack.
You need to be aware of the different types of methods upon which you fall victim of. For the most part, facebook users fall victims of facebook hack due to negligence or not being aware of the right majors to put in place.
Basically, I will discuss 3 major ways or method that hackers uses to gain access to your facekook account. One of the method is nearly impossible for an ordinary hacker to use. The reason is that this method is taken care of by facebook developers and engineers.
For the most part, many users are not usually hacked on facebook. What happened is they grant access to their account without knowing about the basic implications. This normally happens through third party. It can be an installed application on their device, a web site or any other means.
When such happens, users fall victims of nude photo post and other phonographic links posting or sharing on the user behalf.
Please do not grant access to untrustworthy application or web site to your facebook account. Facebook do give you a hint on what you are about to do and at the same time warned you about the implications.
Methods through which hackers gain access to your facebook account
1. Hacking facebook server
Facebook server can be hacked to gain access to users information. Login username, password (encrypted data), email address, bio etc. For the most part, this method is a mirage to even advanced hackers. Note that, in case such happens, your login detail (password) is a hashed key of your original password.
Not withstanding, hashed key can be decrypted (decoded, deciphered); IT jagons!
Decryption
Decryption is the method in which encoded or encrypted (meaningless or unreadable text) data (text, image etc) is being converted into a readable and meaningful text to human. This can be achieved via a manual method or using computer software.
For the most part, facebook team is doing everything humanly and technologically possible to prevent such. Facebook are having the best hackers in the world to keep their server safe from intrusion.
There are many methods under this, such as brute force attack, dictionary attack, cross site scripting and other advanced methods.
What can you do to prevent being victim in such hack?
Virtually nothing!
2. Social Engineering
Internet users usually fall victim of such attack.
What is social engineering?
Social engineering is the act of deceiving and or manipulating people so that you can obtain their personal and or confidential information.
Social engineering is the most common type of attack used by hackers to obtain login details from users. It is easier to deceive people to give you their password than hacking it - Mande Kira
Be vigilant!
The information seek by this type of hackers vary. For the most part, victim is being deceived to give out his username and password. These hackers are specialized in tricking their target victim be it online or physically. They can have access to your computer to secretly install malicious software. This can give the attacker access to your confidential information such as login details, bank information and at the same time take control of your computer. Scary! Right?
Social engineering is a very common type of attack used by hackers. For the most part, I will list some common attacks associated with social engineering. I will also find time to elaborate on each of the methods in time to come.
Most common social engineering attacks
1. Email
Email from your friend is sometimes very dangerous! Yes!
If hacker hacked or gain access to your friends' email, the hacker now have access to that person’s contact list. Once a hacker is having that email account under his control, the hacker can easily send emails to all the person’s contacts with malicious link or attachment which you may end up following link downloading the attachment. For the most part, the content of such email will be so tempting that victims end up following the link or downloading the attachment. And voila! You are now a victim.
Few seconds call can save you a lot! Confirm from your friend he really sent you such email - Mande Kira
2. Phishing
Phishing is a process used by hackers by pretending to disguise as a trustworthy entity to obtain information from their victim. It can be done via email or other means of communication electronically.
Content of the message may varies. You may told that their is a problem with your bank, credit card, file, login details etc. You may also be told that you are a winner of one the most famous competition, lottery etc. It may also be a message asking for help for disaster victims, charity etc.
Be content of what you have, else phishing will surely fish you out!
Generosity is good, but sometimes it lands you in phishers net - Mande Kira
3. Creating distrust
This is one of the most dangerous type of social engineering attack. The hacker does not only gain information from you but also separate you from your friends. When the hacker gain your trust, he then exploit personal information from you.
The time has come when virtual friends are replacing physical friends! - Mande Kira
4. Baiting
Cracked software, application, free movies, free songs etc. Avoid it. As you download, you download with other malicious application on your device. This malicious application might be feeding your activities to the hacking including your raw login details.
Nothing comes for free without freebies going back to the giver - Mande Kira
How not to fall victim of social engineering by hackers
Do not be in a haste. Never rush to clicking on links. Always pay for services or genuine software. Make research. To not believe too good to believe messages. Ask questions. Do not trust virtual friends. Be sincere to yourself. Foreign offers are fake. Secure all your devices. Use a strong password. Avoid using "Remember me" button on device that is not yours. Be wary about public WiFi.
If you are already a victim, change all your passwords. Delete, uninstall any file or application you got illegally. Use strong anti virus and malware detection software.
3. Third party application access
This method is not really a hack. But criminals use it very often and its very rampant. Many facebook users fall victim of such trick. As a developer, you can use your application or web site to request access for information of user from facebook. When user grant access to your application or web site, the application or web site can carry out some activities such as posting, viewing friends, messsaging etc on your behalf. The application or web site can also use the facebook login credentials to log you in. That is a kind of cross site communication. So with facebook logins, you do not have to register on other sites or application. All you do is to link up your facebook to the application and web site.
The main aim of such technological idea is to relieved users from the stress of remembering login details.
How does nude got posted on your facebook page?
You might have granted access to a malicious or untrusted application or web site that can post on your behalf. The application or site is posting nude on your behalf.
How to prevent it
Do not grant access to web site or application you do not trust. When granting access to your facebook account, make sure you read and understand the risks and what the application or web site can do on your behalf. If you are not comfortable with it, do not grant access to it.
How to check and remove access from your facebook account
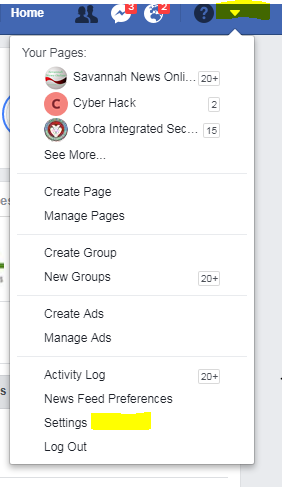
1. Login to your facebook account from facebook web site on computer.
2. Click on the drop down menu at the top right corner as shown on the picture below and click on Settings (highlighted by yellow color).
3. Click on Apps on the left panel site as shown in the picture below (highlighted by yellow color)
4. Hover over any application you want to edit or remove as shown in the picture below (highlighted by yellow color)
5. Edit visibility and other settings after clicking on the Edit pen symbol as shown in the picture above (highlighted by yellow color)
6. Change app activity visibility and other settings if you do not want to remove it as shown in the picture below (highlighted by yellow color)
7. You can now play around with it and make a best decision for yourself.
If you have any question or request on other issues, I will be glad to help. Just drop your question in comment below box.
Please share if it helps you. It also give me courage to write more.




Thank you for the comprehensive post. Now I understand how nude got to my facebook post.
ReplyDeleteYou are welcome! Happy I helped!
Delete